Modern technology is constantly advancing and growing ever more complex. Whilst these advancements can be fantastic they also bring the potential for new threats to our safety and security. One such threat is GNSS or GPS spoofing. In this article, we will attempt to explain GPS spoofing, the different methods used, and how we can better protect ourselves against spoofing.
What is GPS spoofing?
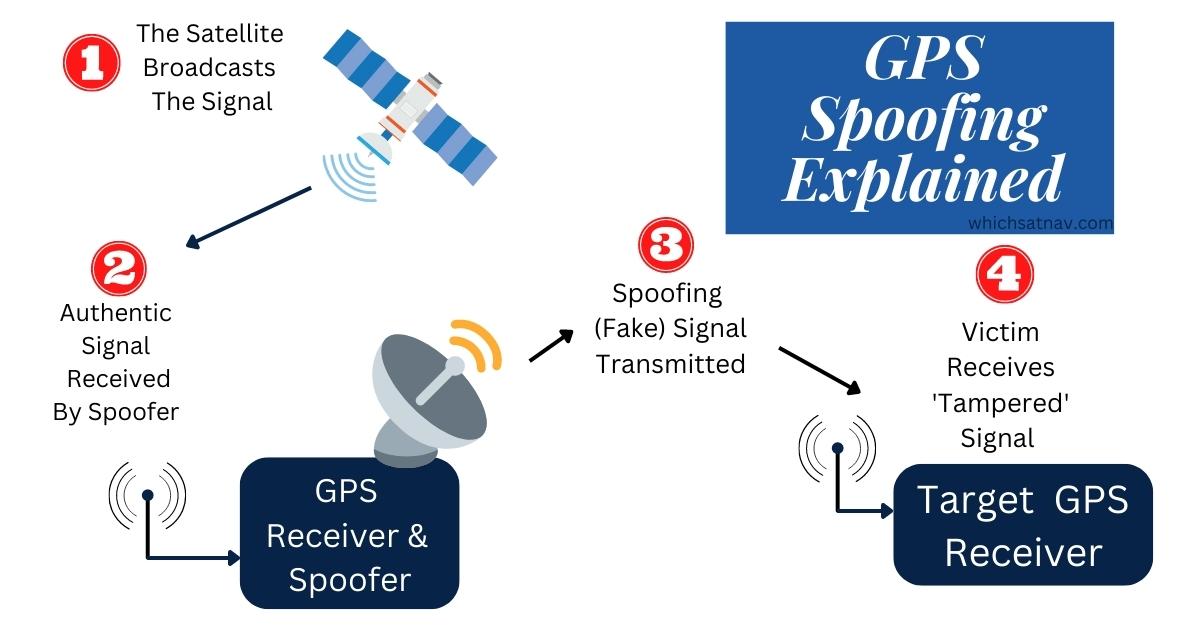
GNSS (or GPS) spoofing is a type of attack where an unauthorized user sends false signals to a GPS receiver in order to trick it into believing it’s located somewhere else.
The goal of GNSS spoofing is usually to confuse and distract the navigating device.
Spoofing can also enable the attacker to do the following:
- Manipulate the GNSS receiver’s clock so that it appears to be out of sync i.e. running slower or faster than it should be
- Transmitting false ephemeris data that could cause the GNSS receiver to place itself at the wrong location
- Inject false almanacs that could cause the GNSS receiver to lose track of which satellites it should be tracking and therefore cause confusion
What is Ephemeris Data?
GPS satellite transmissions contain data about their current location, timing, and “state”. This data is known as ‘ephemeris data‘, and it’s used by GPS receivers to estimate their locations relative to the transmitting satellite. This then enables the receiver to determine their positions on earth.
Types of GNSS / GPS Spoofing Attacks
The ultimate goal of any spoofing attack is to trick a GPS receiver and there are various methods available in order to achieve this deception. Depending upon the methods used, we can categorize the various approaches as follows:
Meaconing Attacks
These types of attacks are probably the most basic type of GNSS spoofing methods. They involve recording the signal received from the satellites at a given location. This signal is then delayed and then retransmitted to the victims’ device at another location.
In the overall scheme of things, meaconing attacks are pretty easy to carry out as the attacker does not have to build the signal from scratch. All it needs is the appropriate front end equipment for the recording of the signal and then a device that is capable of transmitting the recorded signal.
What exactly is Meaconing?
It’s a term used to describe the process of intercepting and then rebroadcasting navigational signals. It is typically done in order to confuse the enemy (or perhaps some competitors) by providing incorrect bearings. In other words, the authentic signals are changed to provide a fake signal which then furnishes a false location.
Nowadays, there are software packages that make things even easier for an attacker. Both the recording and the replaying of the satellite signals can be done with the help of a signal front-end device. For instance, Devices such as the HackRF One, the Adalm Pluto, or the USRP can be connected to your computer and with the help of the software it’s possible to turn them into GNSS receivers.
After recording the signal for a specific duration, another software algorithm can be used to transmit that signal. The attacker won’t, however, enjoy a completely pain-free process as during the transmission of the signal there needs to be a stable clock to generate rock-solid signals.
The Simplistic Spoofing Attack
For a simplistic spoofing attack, a complete signal needs to be designed from scratch. The formulation of a GNSS signal is a fairly straightforward task as both the signal and the message structure are openly available.
These details can be found in the interface control document of the respective system. The fact that this information is so easy to obtain has led to this type of spoofing becoming one of the most common attacks.
GPS simulators are most commonly utilized in order to carry out an oversimplified spoofing attack. These devices can generate the signal for specific locations. Simulators can either be hardware-based or software-developed, which again, results in making these kinds of attacks a little more common in occurrence.
The main drawbacks of this type of attack are that the signals generated through this method are not synchronized. Apart from that, the satellite included in the signal are completely a guess, and it can be different from the real situation.
Intermediate Spoofing Attacks
An intermediate spoofing attack is a more advanced technique that involves using a receiver spoofer. This method involves generating a signal that is as similar to the actual signal as possible.
In the case of an intermediate spoofing attack, the attacker receives an authentic signal from the satellite using a GNSS receiver. The signal components such as phase, amplitude, time, position, and velocity are extracted by the receiver and then fed into the spoofer module.
The spoofer then generates a slightly different signal based on the information it has received. This ‘fake’ signal will have a high resemblance to the authentic one. This will make it much harder to detect which is why often the intermediate spoofing attacks are used in covert operations.
One potential, but a major drawback of this type of attack is the introduction of residual modulation and additional noise that comes from the hardware components of the attacker.
Sophisticated Spoofing Attacks
Sophisticated types of spoofing attacks are the most lethal type of attacks that are extremely difficult to detect. Such types of attacks involve multiple receiver spoofer architectures. The main mechanism involved in these attacks is that all the spoofers are phase-locked, which generates a consistent signal.
Each tracking channel of the victim device is brought under control by matching the correlation peak and gradually increasing the power of the signals. Once all the tracking channels are locked, the attacker can easily manipulate the position information of the victim’s device.
The main challenge in this type of attack is to make all the spoofer phase-locked and that’s where the complexity comes into play. Such types of attacks are often used by nation-states and other highly motivated attackers.
How a GNSS Spoofing Attack Can be Dangerous?
Now that we have discussed the various types of GNSS spoofing attacks, it is important to understand how these attacks can be dangerous.
GNSS signals are used by a wide variety of devices such as drones, cars, ships and even in our smartphones. The manipulation of GNSS signals can cause serious nuisance not just to an individual but also to a nation.
Imagine a shipping scenario in which an attacker spoofs the GNSS signals of a ship. The attacker manipulates the positional information and manages to send the ship off course. This could potentially cause some serious damage to the ship as well as endangering the lives of the people on board.
These types of attacks could also be used to manipulate the positional information of a drone. By spoofing the GNSS signals the drone can be made to land in completely the wrong location or be forced to directly hit an obstacle.
How Can We Protect Ourselves From GNSS Spoofing Attacks?
GNSS Spoofing attacks can be prevented with appropriate countermeasures. Meaconing attacks can be avoided by checking the time consistency of the signal. If the time is not synchronized, it might be a sign that you are receiving a spoofed signal.
Similarly, simplistic spoofing can be countered with the help of automatic gain control and location obfuscation. Automatic gain control can be used to automatically detect and correct signal strength. Location obfuscation is a process in which the position information is not shared with everyone.
Only authorized personnel can have access to the position information. This way even if the attacker manages to spoof GNSS signals, he will not be able to manipulate the position information.
Apart from that, there are various other countermeasures that can be used to protect against GNSS spoofing attacks. These include using multiple GNSS receivers, using only authenticated GNSS signals and encrypting GNSS signals.
Multiple GNSS receivers can be used to cross-check the position information. If the position information provided by one GNSS receiver does not match with the others, it might be a spoofed signal.
Final Thoughts
GPS spoofing may seem initially to be a fairly trivial prank, however, this is a serious kind of interference. GPS spoofing is a threat that can provide some serious leverage by malicious actors to alter the position information of GNSS-equipped devices.